HtB-Mirai-WriteUp
Mirai was an easy box / challenge in www.hackthebox.eu
Project maintained by Ejento Hosted on GitHub Pages — Theme by mattgraham
Welcome to my first WriteUp, which is for the Mirai Box.
Breaking in.
First of all, we have to scan the server for ports. We know that the IP of the Mirai’s box is 10.10.10.48, so we can scan for active ports using the nmap.
nmap -sV -sC -oA output 10.10.10.48
I used the next options
- -sV: Determine service / version information
- -sC: Use default scripts
- -oA: Output in the three major formats at once
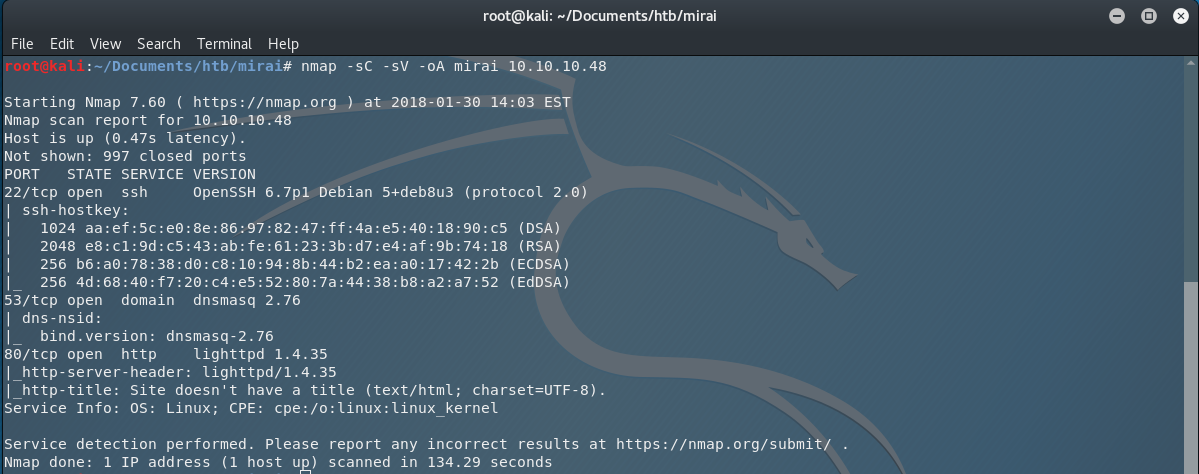
So we are scanning the machine for ports and we found out that the ports 22 (ssh), 53 (dnsmasq) and 80 (http) are active.
Next, let’s open the browser and go to http://10.10.10.48:80
That’s an empty page. Searching for interesting things in the the source code of the page, I found nothing. So let’s try to enumerate the directories of the server. I fire up dirb and I use the common wordlist for the directory scan.
dirb http://10.10.10.48 -r -o mirai.dirb
I used the next options
- -r: Because I don’t want to do a recursive scan. (who has time for that).
- -o: I want to save the results in an output file.
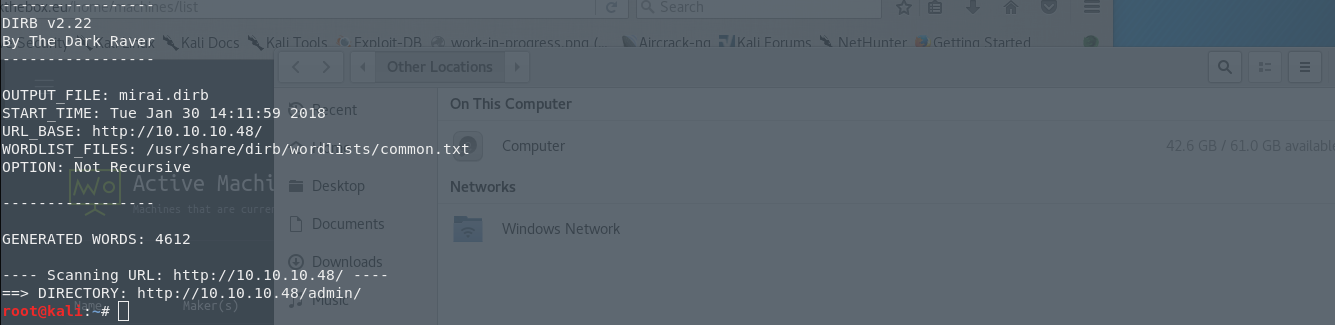
So I have the results, and I have a new directory that I can visit and that is, /admin/. I open the directory in my browser and I have the following page in front of me.
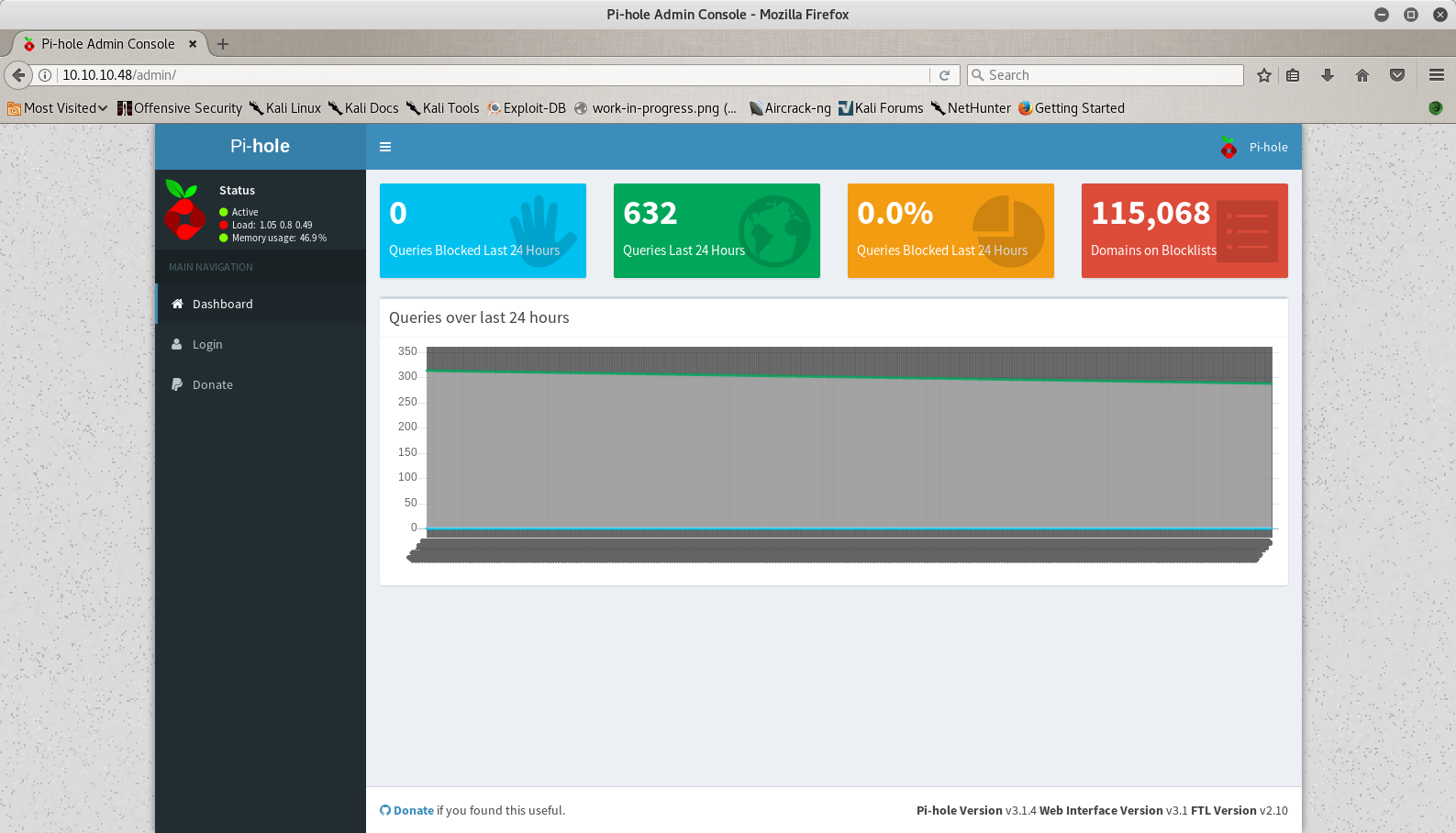
So let’s say that I don’t know what pi-hole is, so my next move is to visit Google. The first result is the url Pi-Hole and if I open the page I can see that is a software for blocking advertisements in a network and we can run it in a raspberry pi. My first thought was to see if I am actually in a raspberry pi, so I searched the web for the default SSH credentials (I knew them already because I have one, but let’s say that I don’t) and in the documentation I found that the default user is pi and the password is raspberry.
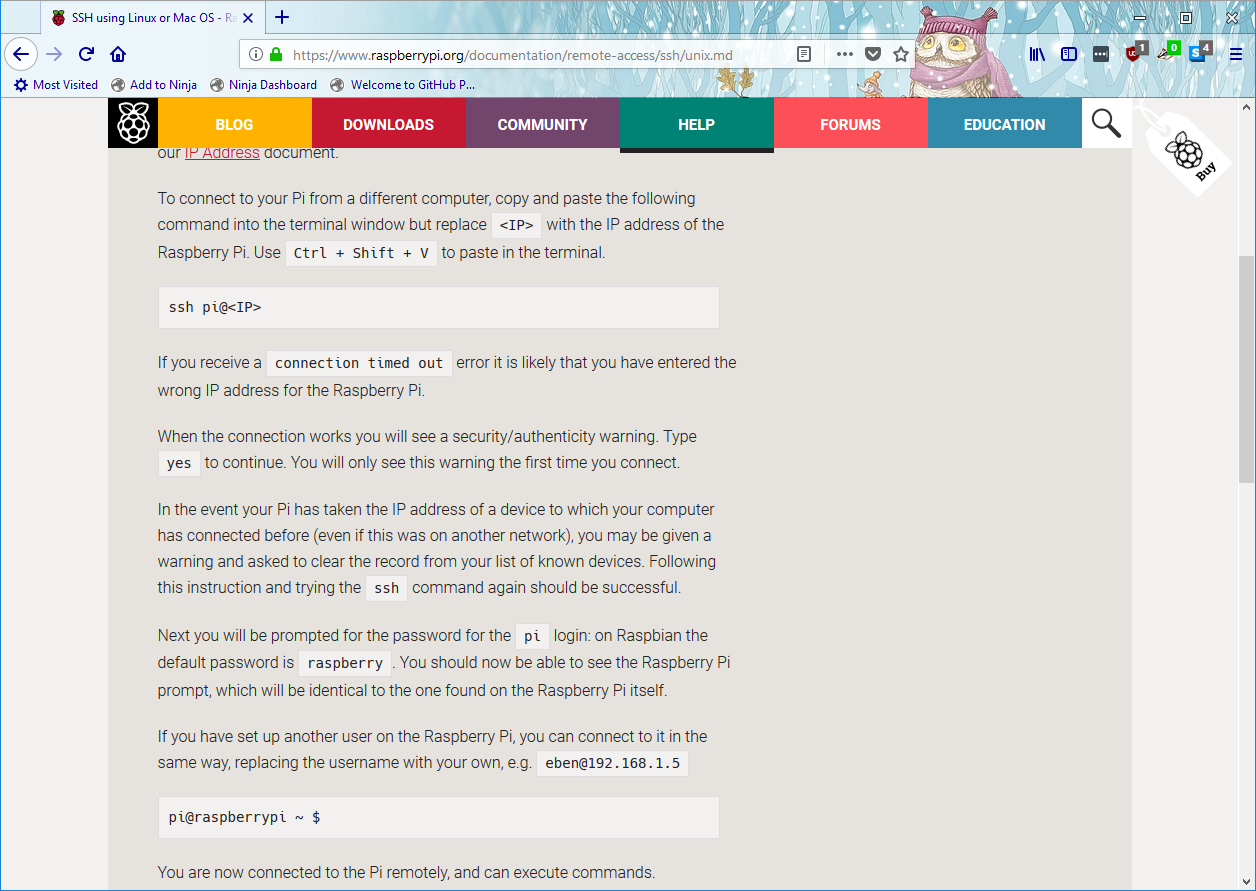
With that knowledge I tried to connect to the SSH port.
ssh pi@10.10.10.48
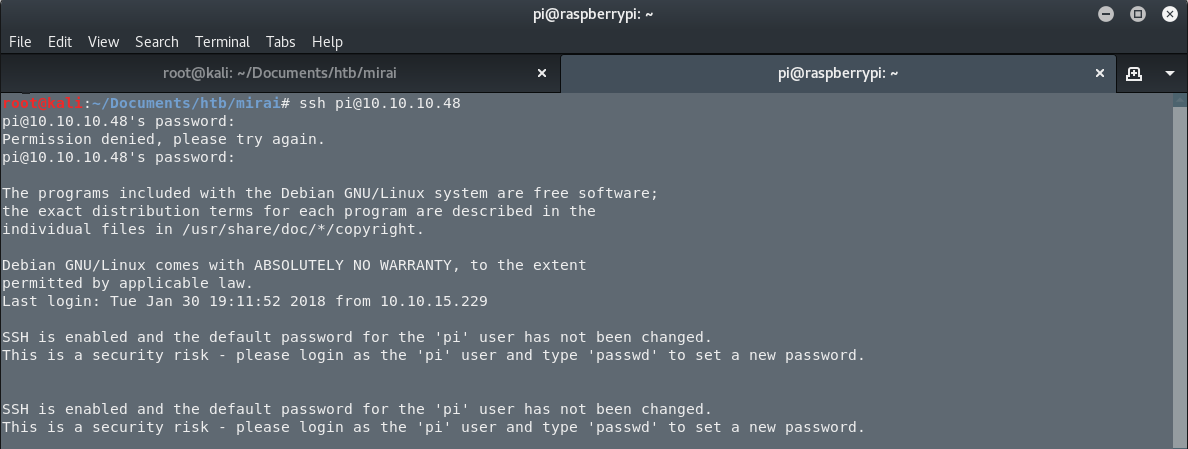
…and I am in. The first step is done. I am in.
Enumeration
As you can see, I am connected in the server as the user pi. But I don’t know what my uid is so I am executing the command id.

So I have the uid 1000. That’s good. Let’s see what commands I can run as root in the server. I am executing the next command sudo -l.
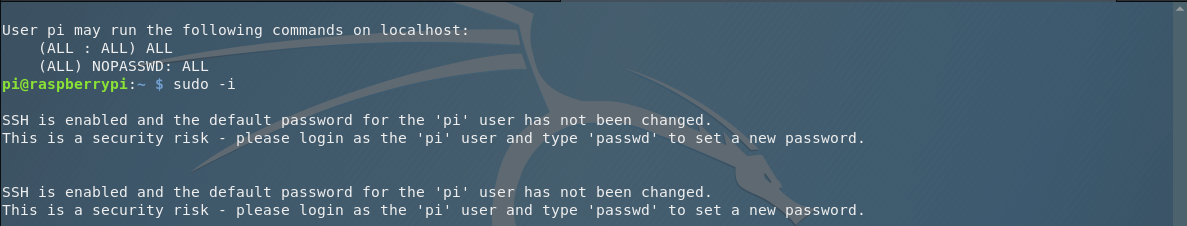
And I can execute ALL the commands as root. So let’s fire up a login shell for the user root. The command is sudo -i. And now, I am the user root in the web server.
Getting the Flags
Searching for the file root.txt in the root’s home directory, I got the next message.
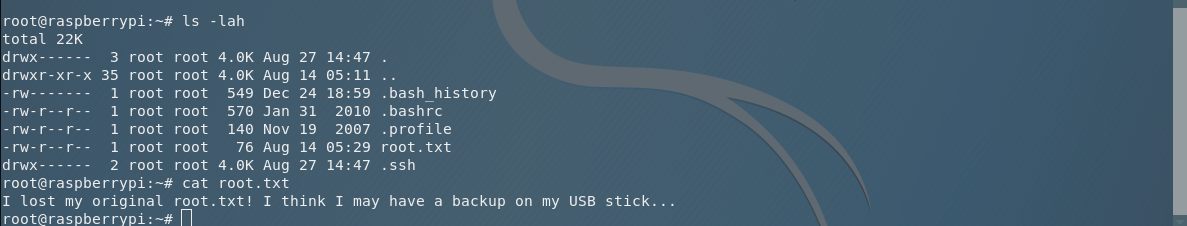
I lost my original root.txt! I think I may have a backup on my USB stick.
So the information I got here is that it is worth a try to search for a USB stick connected to the server. I use the command mount and I have the next interesting results.
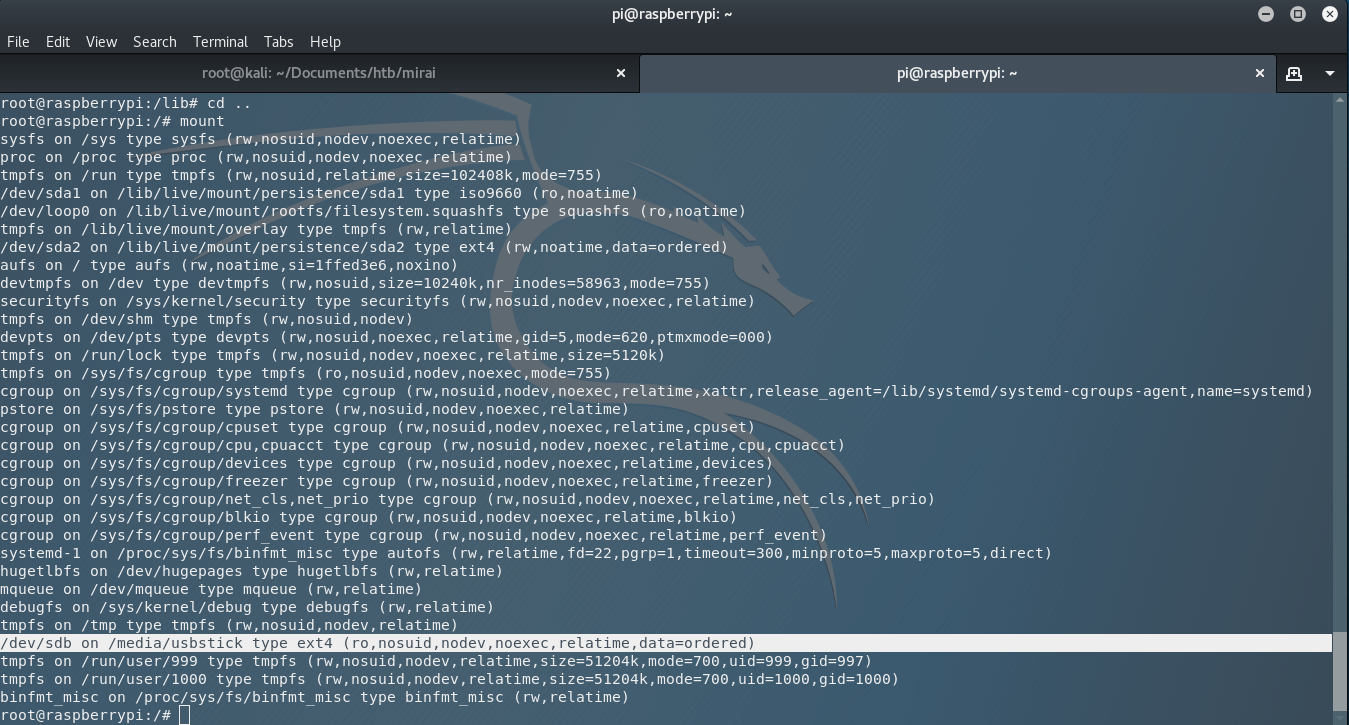
Let’s visit the directory, using the command cd /media/usbstick/ and open the next odd text file that I saw there and that is damnit.txt.
I use cat damnit.txt and I got the next text…..
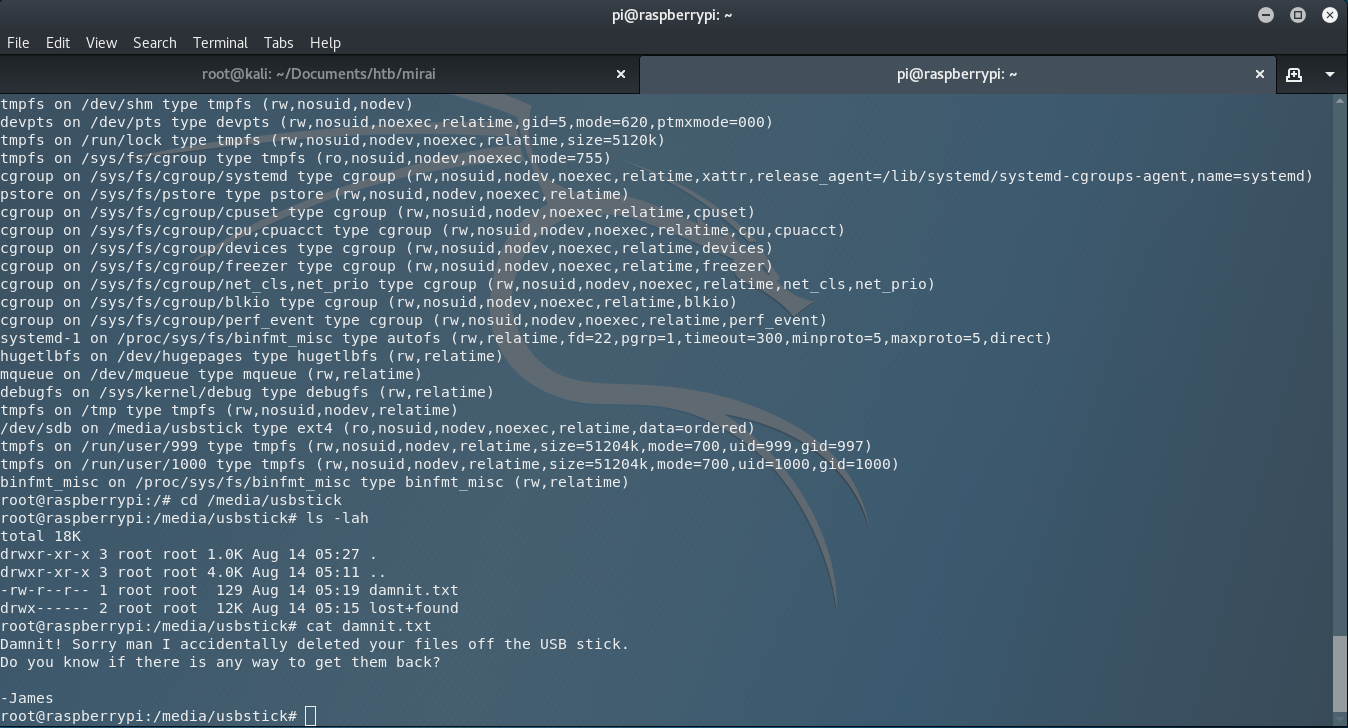
Damnit! Sorry man I accidentally deleted your files off the USB stick. Do you know if there is any way to get them back? -James
Damn you James. What are you doing with my files?!?!, I screamed to my screen.
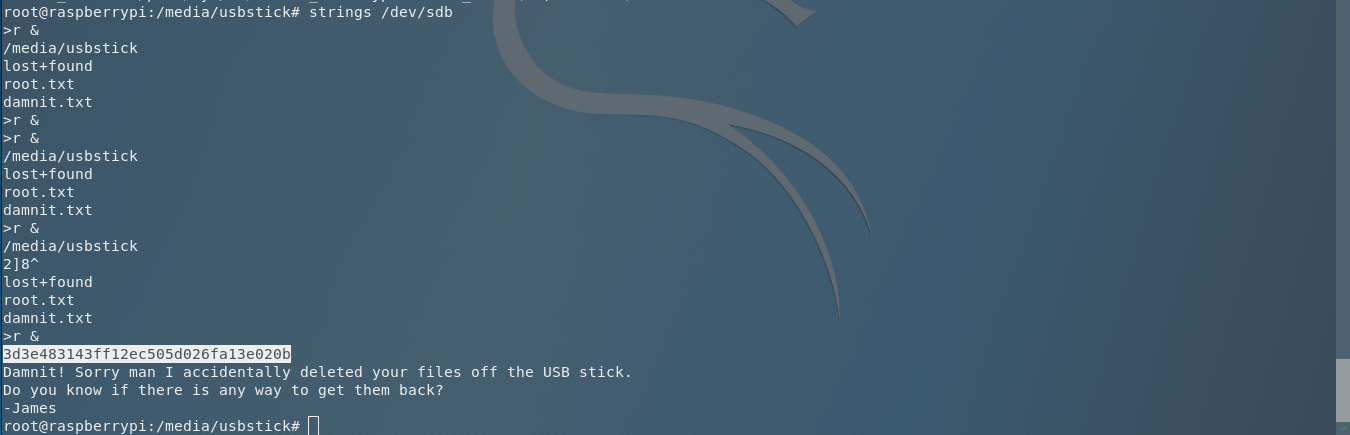
Anyway, let’s take a moment and think about Unix OS. In Unix OS, we say that Everything is a file!. So what does that mean? It means that we can check the entire partition with a command like it is a file, for example strings. So I am executing strings /dev/sdb and I have the root flag, from the text that was inside the root.txt before it got deleted from James.
As you can see, in this run I forgot to find the user flag, so I jumped in again using the ssh and I searched for the user.txt file in the user pi’s home directory.
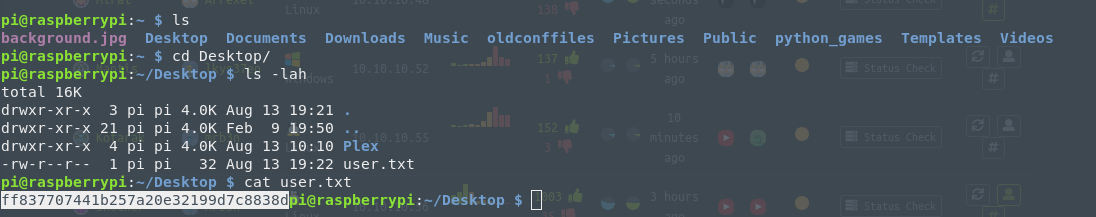
Now we got all the flags. We are done. You can jump in the next challenge and have fun with it.